| Lesson 5 | Specific domain controllers |
| Objective | Define the types of Domain Controllers in Active Directory |
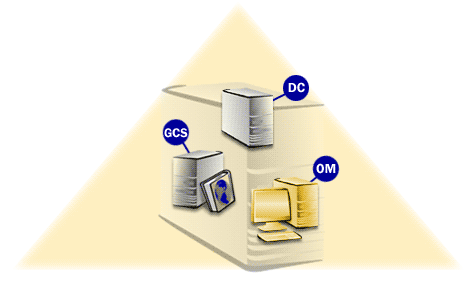
Types of Domain Controllers in Active Directory
Active Directory Domain Services (AD DS) uses a multi-master model: most changes can be written to any writable domain controller (DC) and then replicated.
However, some operations must be coordinated to avoid conflicts or to guarantee uniqueness across the domain or forest. To solve that problem, Active Directory assigns
specific responsibilities to specific domain controllers through a small set of special roles.
What “type” means in this lesson
In day-to-day administration, the phrase “types of domain controllers” is commonly used to describe:
- Standard writable domain controller (AD DS installed, writable directory partitions for its domain)
- Global Catalog server (a DC role that enables forest-wide searches and logons across domains)
- Operations Master (a DC that holds one or more FSMO roles)


1) Standard writable domain controller
A domain controller is a server running Windows Server with Active Directory Domain Services installed. It hosts:
- a writable copy of the directory partitions for its domain (users, groups, computers, OUs, GPO links, and more)
- authentication and authorization services (Kerberos/NTLM, ticket validation, logon processing)
- directory replication (inbound and outbound changes to keep DCs consistent)
2) Global Catalog server
The Global Catalog (GC) is a role that helps users and applications find objects across the entire forest.
A GC-hosting domain controller stores:
- a full replica of its own domain (all attributes, writable)
- a partial replica of every other domain in the forest (a curated attribute set, read-only)
That partial replica is based on the Partial Attribute Set (PAS) defined in the schema. PAS exists to make common forest-wide searches fast, without requiring clients to “bounce” from domain to domain looking for the authoritative partition.
Design guidance:
- Place GCs close to logon and query traffic (often per site) to reduce cross-site latency.
- Use multiple GCs for resilience; clients can automatically use another GC if one is unavailable.
- Be deliberate when changing PAS membership—adding attributes can increase replication and database size.
3) Operations Master (FSMO role holder)
Some operations must be handled by a single authority at a time. Active Directory implements this using
Flexible Single Master Operations (FSMO). There are five FSMO roles:
- Schema Master (forest): controls schema updates
- Domain Naming Master (forest): controls adding/removing domains in the forest
- RID Master (domain): allocates RID pools so security principals get unique SIDs
- PDC Emulator (domain): time coordination, password change priority, legacy compatibility
- Infrastructure Master (domain): updates cross-domain references (for example, group membership references)
A domain controller holding one or more of these roles is commonly referred to as an operations master. Role placement is a design decision: in smaller environments, several FSMO roles are often co-located; in larger environments, you may distribute roles to balance load and reduce risk.
Related domain controller type you will see in production: RODC
Many organizations also deploy a Read-Only Domain Controller (RODC), especially in branch offices or less physically secure locations.
An RODC hosts a read-only copy of the directory partitions and supports authentication with tighter controls around credential caching.
This reduces the impact if a server is stolen or tampered with while still enabling local logon performance.
Building and deploying domain controllers
Deploying a domain controller typically means:
- building the Windows Server host (security baseline, patching, storage, backup strategy)
- installing AD DS and promoting the server to a domain controller
- assigning roles intentionally (GC and/or FSMO where appropriate)
- validating replication, DNS integration, and site/subnet mappings